Amy Sprague
February 3, 2022
Tianhao “Daniel” Xu’s research on creating a simulated task environment to study “spear-phishing” behaviors won the Alphonse Chapanis Best Student Paper at the Human Factors and Ergonomic Society’s (HFES) 2021 Conference.

Tianhao “Daniel” Xu
Unreachable subjects
ISE Ph.D. student Tianhao “Daniel” Xu is trying to do user research on unreachable subjects - the attackers and receivers of spear-phishing emails. Spear phishing is an email scam in which attackers find enough information about their targets to fake a personal or business relationship in order to install malware onto their computers or trick them into unwittingly giving up valuable information.
Studying the behaviors involved in spear-phishing is quite difficult. Daniel explains, “Not only are attackers not recruited for research studies, especially with the risks involved in working with them, but it is really hard to study victim behavior because the information involved is so personal and sensitive.”
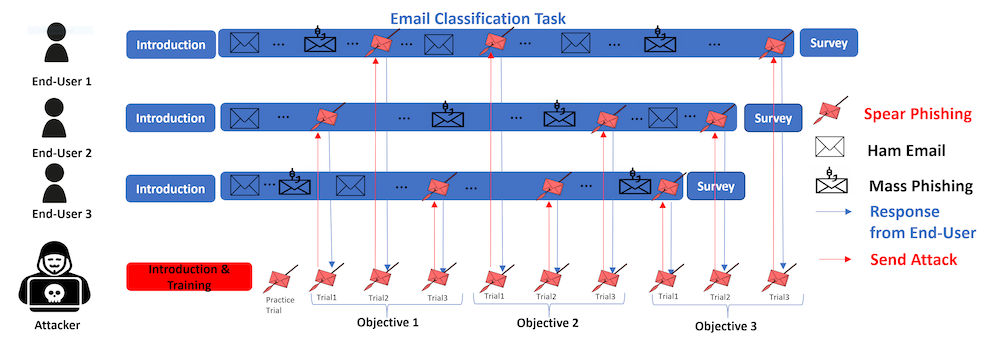
A simulated email task environment
As a response, Daniel created a simulated email task environment, dubbed SpearSim, and recruited students from around the University to test it. For every four students in a virtual test group, three received instructions that they would be performing email sorting tasks. Each was given an identity from the Enron dataset, the most extensive user and email dataset publicly available.
The fourth student received the assigned role of “attacker” and completed a brief training on crafting spear-phishing emails. The attacker received the others’ fictional profiles with varying levels of publicly available personal information and a spear-phishing template. The attackers modified the templates and sent several emails to accomplish three goals for each victim: 1) Harvest bank account credentials, 2) Harvest work account credentials, and 3) Install malware from an attachment.
The attacker sent emails over several rounds that were received with a wider set of emails from the Enron dataset. For each email received, users decided whether to respond to the email, flag it for later, delete it, or block the sender. Attackers gained points when a victim responded.
Contributions to the field
This initial study indicated that the more information that was publicly available, the more successful the spear-phishing campaign. And the attackers in the study adapted their methods based on the feedback they were getting from their users.
Daniel’s adviser and co-author, ISE Assistant Professor Prashanth Rajivan, gives perspective to this simulated environment. “Daniel has developed a novel approach to study attacker and end-user behaviors associated with spear-phishing attacks in a controlled laboratory environment. This approach is expected to spur much-needed research that will reveal factors that make us vulnerable to targeted forms of phishing attacks.”
Daniel knows we can start with a first step, “Be careful what you are revealing about yourself online!”
Access the paper
SpearSim: Design and Evaluation of Synthetic Task Environment for Studies on Spear Phishing Attacks, by Tianhao Xu, Kuldeep Singh, and Prashanth Rajivan.